Cybersecurity and Malware: What You Need to Know
Cybersecurity and Malware: What You Need to Know
By Jennifer Roeder, ProLogic ITS
For February, I wanted to ponder fun in the classroom, such as uplifting additions to add to the daily routine to inspire motivation and bring joy. However, after working with several districts regarding network breaches, I leaned toward sharing cybersecurity and implementing Managed Detection Response (MDR) and its importance.
In one situation, ProLogic ITS was to install a new intercom system for a school located in east Georgia. I received a call at 7 a.m. from the IT Director asking to delay the project. He added, "The FBI called my cell phone at 4:30 a.m. this morning. They reported a Malware attack had hit our district." The IT Director also added it would be several weeks before the teachers, students, and administration would use the school's network. I do not believe any of us would appreciate the "wake-up" call with that type of information.
Luckily, the school district I support has 24/7 malware detection and a plan in place. They were able to contain the incident and sort out how to navigate the district's network safely.
The other situation I am going to share did not settle as quickly. In south central Georgia, an entire district got hit by malware. There was no warning as the district handled its cybersecurity in-house. That means the hours there is no one monitoring the system, the hackers come out to infiltrate. This situation did not have an easy solution. The IT teams tried to contain the attack, but every device on the network needed to be managed and debugged. There was massive collateral, from lost instructional time to an enormous workload for the IT department and a complete disruption in the administrators' records.
Throughout the year of COVID-19, we have pivoted to include more virtual/hybrid education experiences and a push for students to have their own devices. However, a breach can occur due to the network not being safe and secure as the network expands.
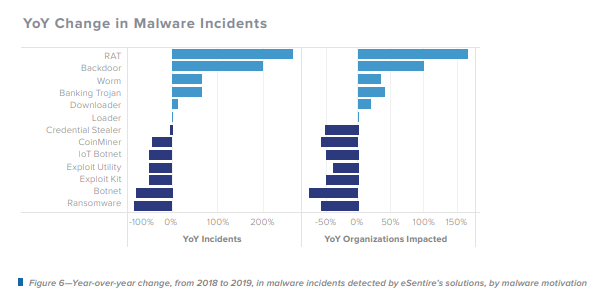
The graph above outlines the change in malware incidents from an assortment of malicious organizations. The graph depicts how the infiltrators adapt tactics to manipulate systems currently in place. The remedy is to combine network security, monitor endpoints, and raise awareness of deception technology, in addition to operating under an expectation of an inevitable breach, employing minimum trust network policies, and having processes in place to respond rapidly to an incident or breach.
After seeing the lingering chaos of Phishing, Malware, and Ransomware, you may wish to have a discussion with your team about a plan if you do not currently have a Managed Detection Response (MDR) in place. I will be happy to support you in assessing and building a comprehensive cybersecurity strategy to safeguard your school.
In the meantime, here are some strategies to implement to Defend Against Phishing:
- Enforce the use of multi-factor authentication for school email accounts
- Introduce procedures for reporting phishing and sharing confirmed reported phishing attempts, which help employees quickly identify phishing indicators
- Deliver phishing awareness training to institute best practices (for example, mousing-over links to inspect them, examining sender details, reporting anything suspicious, not clicking links, contacting/verifying the sender from outside your organization)
- Ensure employees are particularly cautious of generic Office 365-related communications. Additionally, administrators may want to implement rules to redirect emails, including turning storage services links to a monitored inbox.
References:
For more information, see eSentire_Annual-Threat-Intelligence-Report_2019.pdf
 Jennifer Roeder is a former school teacher of six years from Cherokee County, GA. She shares her passion for the implementation of integrated classroom technology, school technology, and professional development. She holds certifications as a Promethean Certified Teacher and a Microsoft Innovative Educator. Jennifer is proud to be part of the ProLogic ITS team focusing on current school technology integration and STEM education.
Jennifer Roeder is a former school teacher of six years from Cherokee County, GA. She shares her passion for the implementation of integrated classroom technology, school technology, and professional development. She holds certifications as a Promethean Certified Teacher and a Microsoft Innovative Educator. Jennifer is proud to be part of the ProLogic ITS team focusing on current school technology integration and STEM education.
